What is Ansible?
Ansible is an open source automation and orchestration tool for software provisioning, configuration management, and software deployment. Ansible can easily run and configure Unix-like systems as well as Windows systems to provide infrastructure as code. It contains its own declarative programming language for system configuration and management.
Ansible is popular for its simplicity of installation, ease of use in what concerns the connectivity to clients, its lack of agent for Ansible clients.
Since it uses SSH, it can very easily connect to clients using SSH-Keys, simplifying though the whole process. Client details, like hostnames or IP addresses and SSH ports, are stored in files called inventory files. Once you have created an inventory file and populated it, ansible can use it.
Important terms used in Ansible
Ansible server: The machine where Ansible is installed and from which all tasks and playbooks will be ran
Module: Basically, a module is a command or set of similar Ansible commands meant to be executed on the client-side
Task: A task is a section that consists of a single procedure to be completed
Role: A way of organizing tasks and related files to be later called in a playbook
Fact: Information fetched from the client system from the global variables with the gather-facts operation
Inventory: File containing data about the ansible client servers. Defined in later examples as hosts file
Play: Execution of a playbook
Handler: Task which is called only if a notifier is present
Notifier: Section attributed to a task which calls a handler if the output is changed
Tag: Name set to a task which can be used later on to issue just that specific task or group of tasks.
Playbooks: Lists of tasks that automatically execute against hosts
Ad-hoc Commands: Uses the /usr/bin/ansible command-line tool to automate a single task on one or more managed nodes. ad hoc commands are quick and easy, but they are not reusable
Install Ansible on Centos/RedHat systems
Step 1) Lets install wget, vim and tree packages then download the EPEL repository and install it.
# yum install wget vim tree
# wget https://dl.fedoraproject.org/pub/epel/epel-release-latest-7.noarch.rpm
# yum install epel-release
Step 2) Once the EPEL repository is install start install of ansible package
# yum install -y ansible
Step 3) Lets create ansible user on all servers.
# useradd ansible -c "ansible" ; echo pass@1234 | passwd --stdin ansible
# echo "ansible ALL=(ALL) NOPASSWD: ALL" >> /etc/sudoers
# ssh-keygen
Step 4) Create password less connection from ansible server to clients.
# ssh-copy-id ansible-clients
Ansible installation is completed.
Below the Ansible modules used by most of System Administration:
- Software packages installation.
- Services
- Firewall rule -- firewalld
- File system -- parted
- File content -- file
- Archiving -- archive
- Scheduling Tasks - Cron
- Security -- yum
- Users and Groups -- user
- Shell
- script
Let start with Ansible Inventory
- In an Ansible, managed hosts or servers which are controlled by the Ansible control node are defined in a host inventory file. By default location of host file is "/etc/ansible/hosts".
- You can specify a different inventory file using the -i <location of inventory> option while using the ansible command.
- There are two types of inventory files in Ansible that is Static and Dynamic.
Let start with simple inventory file which contain group and hostname.
[ansible@ans01 ~]$ cat /etc/ansible/hosts
[kvm-base]
kvm01
kvm02
[centos]
kvm01
lamp01
zap01
pup01
dock01
[redhat]
kvm02
web01
db01
ans01
[ubuntu]
wpress01
[suse]
suse01
[windows]
win01
[web]
lamp01
zap01
web01
[db]
lamp01
zap01
db01
Let start with little advance inventory lists which contains connection, protocol, user, password, arrays
[ansible@ans01 ~]$ cat /etc/ansible/hosts
kvm01 ansible_connection=ssh anssible_user=root ansible_ssh_pass=redhat
kvm02 ansible_connection=ssh anssible_user=root ansible_ssh_pass=redhat
lamp01 ansible_connection=ssh anssible_user=root ansible_ssh_pass=redhat
zap01 ansible_connection=ssh anssible_user=root ansible_ssh_pass=redhat
pup01 ansible_connection=ssh anssible_user=root ansible_ssh_pass=redhat
dock01 ansible_connection=ssh anssible_user=root ansible_ssh_pass=redhat
web01 ansible_connection=ssh anssible_user=root ansible_ssh_pass=redhat
db01 ansible_connection=ssh anssible_user=root ansible_ssh_pass=redhat
ans01 ansible_connection=ssh anssible_user=root ansible_ssh_pass=redhat
wpress01 ansible_connection=ssh anssible_user=root ansible_ssh_pass=redhat
suse01 ansible_connection=ssh anssible_user=root ansible_ssh_pass=redhat
win01 ansible_connection=winrm ansible_user=administrator ansible_password=Azure#12345678
[web] ### GROUPS NAME ##
lamp01
zap01
web01
wpress01
[db]
lamp01
zap01
db01
wpress01
[kvm]
kvm0[1:2] ## ARRAY OF SERVERS ##
[ansible@ans01 ~]$
List the host using centos and redhat groups
[ansible@ans01 ~]$ ansible --list-hosts centos
hosts (2):
centos-vm1
centos-vm2
[ansible@ans01 ~]$ ansible --list-hosts redhat
hosts (2):
redhat-vm1
redhat-vm2
The below command will help to get the complete system information of pup01 servers.
[ansible@ans01 ~]$ ansible -m setup pup01
The below command will help to list the modules installed.
# ansible-doc -l
To Check the attribute of the module
# ansible-doc -s ping
# ansible-doc -s shell
# ansible-doc -s copy
# ansible-doc -s file
# ansible-doc -s yum
# ansible-doc -s service
# ansible-doc -s parted
# ansible-doc -s archive
# ansible-doc -s firewalld
# ansible-doc -s cron
# ansible-doc -s user
Let start with Ad-hoc Commands with modules
In Ansible AD-HOC command uses to automate a single task on one or more managed nodes. AD-HOC commands are quick and easy, but they are not reusable
Why use AD-HOC commands?
AD-HOC commands are great for tasks you repeat rarely. For example, if you want to power off all the machines in your lab for vacation, you could execute a quick one-liner in Ansible without writing a playbook. An AD-HOC command looks like this:
$ ansible [group/Server] -m [module] -a "[module options]" -u [user name] --become
-B Seconds
-k (ask password)
-T TIMEOUT
-a Module_ARGS
-b become
-m module
-v or -vvv or -vvvv
Example of Ad-hoc
To check the uptime of all servers.
[ansible@ans01 ~]$ ansible all -a uptime
If user account is not created password less login you can use this option.
[root@ans01 ~]# ansible centos -a uptime --ask-pass
if you want to disable ssh host check you can uncomment the below line.
[root@ans01 ansible]# cat /etc/ansible/ansible.cfg | grep host_key_checking
#host_key_checking = False
[root@ans01 ansible]#
[ansible@ans01 ~]$ ansible redhat -a whoami -i inventory.txt
[root@ans01 ansible]# ansible centos -a whoami -i /home/ansible/inventory.txt --ask-pass
The below command required sudo rights, hence use -b parameter.
$ ansible all -a "uname -a"
$ ansible all -a 'dmidecode' -b | grep -A5 "System Information"
$ ansible all -a " systemctl restart rsyslog"
$ ansible all -a " systemctl restart rsyslog" -b
If you need the output in table format use -o parameter.
$ ansible all -m ping -o
$ ansible all -a "uname -a" -o
$ ansible all -a uptime -o
Example of ping module
$ ansible all -m ping
Example of shell module
$ ansible all -m shell -a "mkdir /etc/backup-yum-repos.d" -b
$ ansible all -m shell -a "mv /etc/yum.repos.d/* /etc/backup-yum-repos.d/" -b
Note: Command & Shell Module
The command module allows administrator to quickly execute remote command on managed hosts. These command are not processed by shell on the managed hosts. As such they cannot access shell environment variables or perform shell operations such as redirection and piping
For situation where command require shell processing, administrators can use the shell module.
Example of Command module:
$ ansible all -a 'dmidecode' -b | grep -A5 "System Information"
Example of Shell module:
# ansible all -m shell -a 'dmidecode | grep -A5 "System Information"' -b
Example of copy module
$ ansible centos -m copy -a "src=/home/vdarole/direct/centos.repo dest=/etc/yum.repos.d/centos.repo" -b
$ ansible redhat -m copy -a "src=/home/vdarole/direct/redhat.repo dest=/etc/yum.repos.d/redhat.repo" -b
Example of file module
[vdarole@centos-vm1 data]$ ll
total 0
-rw-------. 1 vdarole vdarole 0 Jan 31 16:13 a
-rw-------. 1 root root 0 Jan 31 16:13 b
-rw-rw-r--. 1 vdarole vdarole 0 Jan 31 16:13 c
[vdarole@centos-vm1 data]$
$ ansible centos -m file -a "dest=/home/vdarole/data/a mode=600"
$ ansible centos -m file -a "dest=/home/vdarole/data/b mode=600 owner=root group=root" -b
$ ansible centos -m file -a "dest=/home/vdarole/data/d mode=600 owner=root group=root state=directory" -b
$ ansible centos -m file -a "dest=/home/vdarole/data/c state=absent" -b
Example of yum module (This module is only used in Redhat or Centos)
$ansible all -m yum -a 'name=net-tools state=installed' -b
$ ansible all -m yum -a 'name=net-tools state=latest' -b
$ ansible all -m yum -a 'name=net-tools state=absent' -b
Example of service module
$ ansible all -m service -a "name=ntpd state=started" -b
$ ansible all -m service -a "name=ntpd state=restarted" -b
$ ansible all -m service -a "name=ntpd state=stopped" -b
Example of cron module
$ ansible redhat -m cron -a "hour=17 minute=15 job=/home/vdarole/date.sh "
$ ansible centos -m cron -a "hour=17 minute=15 job=/home/vdarole/date.sh user=root" -b
$ ansible centos -m cron -a "minute=*/15 job=/home/vdarole/date.sh "
Example of user module
$ ansible all -m user -a "name=admin " -b
$ ansible all -m user -a "name=admin state=absent" -b
Example of archive module
$ ansible lamp01 -m archive -a "path=/home/ansible/archive dest=/tmp/data.tgz"
PLAYBOOK FOR ANSIBLE
All the playbook are written in YAML (Yet another Markup Language)
* Playbook begin with ---
* Comments begin with #hash
* Members of linux begain with -
* Playbook ends with ...
* Key value pairs
<key>: <value>
Lets create our first playbook for ping the servers.
[ansible@ans01 ~]$ cat ping-test.yml
---
- name: first playbook ping test.
hosts: all
tasks:
- name: ping test
ping:
[ansible@ans01 playbook]$
Check the syntax used in playbook
[ansible@ans01 playbook]$ ansible-playbook --syntax-check ping-test.yml
playbook: ping-test.yml
[ansible@ans01 playbook]$
Execute the playbook
PLAYBOOK FOR CREATING USERS.
[ansible@ans01 playbook]$ sudo cat /etc/shadow | grep sysadmin
ansible:$6$N6iHr8MV$0L9ZLHubaTwbib1qWtV4NtBGv489RVRy2IjoId5W0gUZtKJi22uJG3E6ouKgQXPZSQ.YjtdawSFkBPe7Mw3vt1:19086:0:99999:7:::
[ansible@ans01 playbook]$
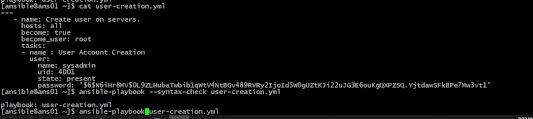
[ansible@ans01 ~]$ cat user-creation.yml
---
- name: Create user on servers.
hosts: all
become: true
become_user: root
tasks:
- name : User Account Creation
user:
name: sysadmin
uid: 4001
state: present
password: '$6$N6iHr8MV$0L9ZLHubaTwbib1qWtV4NtBGv489RVRy2IjoId5W0gUZtKJi22uJG3E6ouKgQXPZSQ.YjtdawSFkBPe7Mw3vt1'
[ansible@ans01 ~]$ ansible-playbook --syntax-check user-creation.yml
playbook: user-creation.yml
[ansible@ans01 ~]$ansible-playbook -C user-creation.yml ## Dry Check
[ansible@ans01 ~]$ansible-playbook user-creation.yml --step
PLAYBOOK FOR INSTALLATION OF WEB SERVER.
ansible@ans01 ~]$ cat webserver-installation.yml
---
- name: Web server Installation.
hosts: centos-vm1
become: true
become_user: root
tasks:
- name : Installation of Apache Package
yum:
name: httpd
state: present
- name : Creation of Index.html
copy:
content: "Welcome to Linux Automation classes"
dest: /var/www/html/index.html
- name : HTTP Service
service:
name: httpd
state: started
enabled: true
---
[ansible@ans01 ~]$ cat mariadb-installation.yml
---
- name: MariaDB Server Installation.
hosts: db
become: true
become_user: root
tasks:
- name: Installation of MariaDB
yum:
name: mariadb, mariadb-server, MySQL-python
state: present
# name: mariadb-server
# state: present
- name: MariaDB Service start and enable
service:
name: mariadb
state: started
enabled: true
- name: mysql_root_password
mysql_user:
name: root
host: localhost
password: redhat
login_user: root
check_implicit_admin: yes
priv: "*.*:ALL,GRANT"
...
[ansible@ans01 ~]$
ANSIBLE VARIABLES
* Varibles name should be letters, number and underscores
* Should always start with a letters
* Not valid variable examples
Vallabh-Darole
Vallabh Darole
13
EXAMPE OF VARIABLES (STATUS)
[ansible@ans01 playbook]$ cat disible_selinx.yml
---
- name: To Disable SELinux.
hosts: all
become: true
become_user: root
vars:
status: disabled
tasks:
- name: Changing the status of SELinux frpm Config file
lineinfile:
path: /etc/selinux/config
regexp: '^SELINUX='
line: 'SELINUX={{ status }}'
--
[ansible@ans01 playbook]$ ansible-playbook disible_selinx.yml --syntax-check
playbook: disible_selinx.yml
[ansible@ans01 playbook]$ ansible-playbook disible_selinx.yml
PASSING THE VARIABLES (STATUS) FROM OUTSIDE
[ansible@ans01 playbook]$ ansible-playbook disible_selinx.yml -e status=enforcing
ANSIBLE CONDITIONAL VARIABLES AND LOOPS
[ansible@ans01 playbook]$ cat start-web-service.yml
---
- name: Start apache service if centos-vm2 is up
hosts: all
become: true
become_user: root
tasks:
- service: name=httpd state=restarted
when: ansible_host == "centos-vm1"
...
[ansible@ans01 playbook]$
[ansible@ans01 playbook]$ cat basic-package.yml
---
- name: Install multple packages
hosts: centos
become: true
become_user: root
tasks:
- name: Install packages
yum: name={{item}} state=latest
with_items:
- ntp
- net-tools
- telnet
- wget
- nfs-utils
...
[ansible@ans01 playbook]$
Ansible Vault
Ansible Vault is a feature of ansible that allows you to keep sensitive data such as passwords or keys in encrypted files, rather than as plaintext in playbooks or roles. These vault files can then be distributed or placed in source control.
ansible-vault [create|decrypt|edit|encrypt|encrypt_string|rekey|view]
To create a new encrypted data file
[ansible@ans01 vault]$ ansible-vault create Check-Uptime.yml
New Vault password:
Confirm New Vault password:
- name: To check system update time.
hosts: all
tasks:
- name: System Uptime
shelli: uptime
To edit the encrypted data file
[ansible@ans01 vault]$ansible-vault edit Check-Uptime.yml
Vault password:
- name: To check system update time.
hosts: all
tasks:
- name: System Uptime
shell: uptime
Check the data file, you wont be able to see code.
[ansible@ans01 vault]$cat Check-Uptime.yml
Run the playbook, it will not work.
[ansible@ans01 vault]$ ansible-playbook Check-Uptime.yml
ERROR! Attempting to decrypt but no vault secrets found
To run the playbook you need to get password from vault using below command.
[ansible@ans01 vault]$ ansible-playbook Check-Uptime.yml --ask-vault-pass
Vault password:
Store the password in file and excute the command.
[ansible@ans01 vault]$ echo "redhat" >> password-file
[ansible@ans01 vault]$ ansible-playbook Check-Uptime.yml --vault-password-file password-file
If you want to reset the password of file below is command.
[ansible@ans01 vault]$ ansible-vault rekey Check-Uptime.yml
Vault password:
New Vault password:
Confirm New Vault password:
Rekey successful
[ansible@ans01 vault]$
If you want to decrypt the playbook below is the command.
[ansible@ans01 vault]$ ansible-vault decrypt Check-Uptime.yml
Vault password:
Decryption successful
[ansible@ans01 vault]$ cat Check-Uptime.yml
---
- name: To check system update time.
hosts: all
tasks:
- name: System Uptime
shell: uptime
...
[ansible@ans01 vault]$
To disable ssh host check.
[ansible@ans01 ~]$ cat /etc/ansible/ansible.cfg | grep host_key_checking
#host_key_checking = False
[ansible@ans01 ~]$ sudo vi /etc/ansible/ansible.cfg
[ansible@ans01 ~]$ su - sysadmin
Password:
Last login: Fri Apr 15 10:34:12 EDT 2022 on pts/2
[sysadmin@ans01 ~]$ ansible all -a "uname -a" --ask-pass
SSH password:
centos-vm1 | CHANGED | rc=0 >>
Linux centos-vm1 3.10.0-327.el7.x86_64 #1 SMP Thu Nov 19 22:10:57 UTC 2015 x86_64 x86_64 x86_64 GNU/Linux
centos-vm2 | CHANGED | rc=0 >>
Linux centos-vm2 3.10.0-327.el7.x86_64 #1 SMP Thu Nov 19 22:10:57 UTC 2015 x86_64 x86_64 x86_64 GNU/Linux
kvm-base01 | CHANGED | rc=0 >>
Linux kvm-base01 3.10.0-1160.59.1.el7.x86_64 #1 SMP Wed Feb 23 16:47:03 UTC 2022 x86_64 x86_64 x86_64 GNU/Linux
redhat-vm2 | CHANGED | rc=0 >>
Linux redhat-vm2 3.10.0-327.el7.x86_64 #1 SMP Thu Oct 29 17:29:29 EDT 2015 x86_64 x86_64 x86_64 GNU/Linux
redhat-vm1 | CHANGED | rc=0 >>
Linux redhat-vm1 3.10.0-327.el7.x86_64 #1 SMP Thu Oct 29 17:29:29 EDT 2015 x86_64 x86_64 x86_64 GNU/Linux
ans01 | CHANGED | rc=0 >>
Linux ans01 3.10.0-1160.59.1.el7.x86_64 #1 SMP Wed Feb 23 16:47:03 UTC 2022 x86_64 x86_64 x86_64 GNU/Linux
[sysadmin@ans01 ~]$
For more details regarding module refer the below links
https://docs.ansible.com/ansible/latest/collections/index_module.html#ansible-builtin
Automation of Lamp01 Project:
[root@kvm01 ~]# virt-clone --connect qemu:///system --original backup --name lamp01 -f /kvm-store/lamp01.img
[root@kvm01 ~]# virsh start lamp01
[root@kvm01 ~]# ssh 192.168.2.219
[root@backup01 ~]# hostnamectl set-hostname lamp01.darole.org
[root@backup01 ~]# sed -i 's/192.168.2.219/192.168.2.211/g' /etc/sysconfig/network-scripts/ifcfg-eth0
[root@backup01 ~]# sed -i 's/enforcing/disabled/g' /etc/selinux/config
[root@backup01 ~]# systemctl disable firewalld
[root@backup01 ~]# reboot
[root@lamp01 ~]# sh puppet-installation.sh
[root@lamp01 ~]# /bin/echo "ansible ALL=(ALL) NOPASSWD: ALL" >> /etc/sudoers
[root@pup01 ~]# puppetserver ca list
[root@pup01 ~]# puppetserver ca sign --all
[ansible@ans01 lamp01]$ ssh-copy-id lamp01
[ansible@ans01 lamp01]$ ansible-playbook webserver-installation.yml
[ansible@ans01 lamp01]$ ansible-playbook mariadb-installation.yml
[ansible@ans01 lamp01]$ ansible-playbook php-installation.yml
[ansible@ans01 lamp01]$ ansible-playbook create-database.yml -e "dbname=database123"
[ansible@ans01 lamp01]$ ansible-playbook create-table.yml
[ansible@ans01 lamp01]$ ansible-playbook copy-web-pages.yml
[ansible@ans01 lamp01]$ ansible-playbook webserver-installation.yml --tags "Restart Webservice"
Automation of Web01 and DB01 Project:
[root@kvm02 ~]# virt-clone --connect qemu:///system --original backup --name web01 -f /kvm-store/web01.img
[root@kvm02 ~]# virt-clone --connect qemu:///system --original backup --name db01 -f /kvm-store/db01.img
[root@kvm02 ~]# virsh start web01
[root@kvm01 ~]# ssh 192.168.2.229
[root@backup01 ~]# hostnamectl set-hostname web01.darole.org
[root@backup01 ~]# sed -i 's/192.168.2.229/192.168.2.221/g' /etc/sysconfig/network-scripts/ifcfg-eth0
[root@backup01 ~]# sed -i 's/enforcing/disabled/g' /etc/selinux/config
[root@backup01 ~]# systemctl disable firewalld
[root@backup01 ~]# reboot
[root@kvm02 ~]# virsh start db01
[root@kvm02 ~]# ssh 192.168.2.229
[root@backup01 ~]# hostnamectl set-hostname db01.darole.org
[root@backup01 ~]# sed -i 's/192.168.2.229/192.168.2.222/g' /etc/sysconfig/network-scripts/ifcfg-eth0
[root@backup01 ~]# sed -i 's/enforcing/disabled/g' /etc/selinux/config
[root@backup01 ~]# systemctl disable firewalld
[root@backup01 ~]# reboot
[root@pup01 ~]# puppetserver ca clean --certname web01.darole.org
[root@pup01 ~]# puppetserver ca clean --certname db01.darole.org
[root@web01 ~]# sh puppet-installation.sh
[root@db01 ~]# sh puppet-installation.sh
[root@pup01 ~]# puppetserver ca list
[root@pup01 ~]# puppetserver ca sign --all
[root@web01 ~]# /opt/puppetlabs/bin/puppet agent --test
[root@web01 ~]# /bin/echo "ansible ALL=(ALL) NOPASSWD: ALL" >> /etc/sudoers
[root@db01 ~]# /opt/puppetlabs/bin/puppet agent --test
[root@db01 ~]# /bin/echo "ansible ALL=(ALL) NOPASSWD: ALL" >> /etc/sudoers
[ansible@ans01 ~]$ ssh-copy-id web01
[ansible@ans01 ~]$ ssh-copy-id db01
[ansible@ans01 web-db]$ ansible-playbook repo-pages.yml
[ansible@ans01 web-db]$ ansible-playbook webserver-installation.yml
[ansible@ans01 web-db]$ ansible-playbook mariadb-installation.yml
[ansible@ans01 web-db]$ ansible-playbook php-installation.yml
[ansible@ans01 web-db]$ ansible-playbook create-database.yml -e "dbname=database123"
[ansible@ans01 web-db]$ ansible-playbook create-table.yml
[ansible@ans01 web-db]$ ansible-playbook copy-web-pages.yml
[ansible@ans01 web-db]$ ansible-playbook webserver-installation.yml --tags "Restart Webservice"
Automation of zabbix Project:
[root@kvm01 ~]# virt-clone --connect qemu:///system --original backup --name zap01 -f /kvm-store/zap01.img
[root@kvm01 ~]# virsh start zap01
[root@kvm01 ~]# virsh console zap01
[root@backup01 ~]# hostnamectl set-hostname zap01.darole.org
[root@backup01 ~]# sed -i 's/192.168.2.219/192.168.2.212/g' /etc/sysconfig/network-scripts/ifcfg-eth0
[root@backup01 ~]# sed -i 's/enforcing/disabled/g' /etc/selinux/config
[root@backup01 ~]# systemctl disable firewalld
[root@backup01 ~]# reboot
[root@zap01 ~]# sh puppet-installation.sh
[root@pup01 ~]# puppetserver ca list
[root@pup01 ~]# puppetserver ca sign --all
[root@zap01 ~]# /bin/echo "ansible ALL=(ALL) NOPASSWD: ALL" >> /etc/sudoers
[ansible@ans01 lamp01]$ ssh-copy-id zap01
[ansible@ans01 lamp01]$ ansible-playbook z-webserver-installation.yml
[ansible@ans01 zabbix]$ ansible-playbook z-epel-installation.yml
[ansible@ans01 zabbix]$ ansible-playbook z-php-installation.yml
[ansible@ans01 lamp01]$ ansible-playbook z-mariadb-installation.yml
[ansible@ans01 zabbix]$ ansible-playbook z-zabbix-installation.yml
[ansible@ans01 zabbix]$ ansible-playbook z-create-table.yml
[ansible@ans01 zabbix]$ ansible-playbook z-zabbix-service.yml




No comments:
Post a Comment